CloudForms and ManageIQ allow the definition of Compliance Policies which can be used to verify consistency of Virtual Machines, Instances, Hypervisors and other objects, in the entire environment. Compliance Policies can trigger actions to be able to notify about non-compliance or to go one step further and enforce compliance, for example by using Ansible Playbooks to fix the problem.
There are a number of examples about Compliance Policies on the official Red Hat CloudForms blog.
Adjust the Smart State Analysis Profile
A separate blog post goes into details on how to create and modify a Smart State Analysis Profile. When creating the profile, it is important its name is “default” and the policy retrieves the content of the file /etc/sysconfig/selinux.
Control Policies
Policies in CloudForms and ManageIQ are always a combination of three items:
-
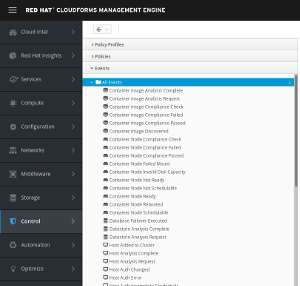
Event: the event triggers the evaluation of the condition. An event can be something like “VM Power On”, “Analysis completed” and many more. A list of out of the box events can be found by clicking on Control, Explorer, and then clicking on Events in the accordion on the left
The screenshot only shows a subset of all available events.
-
Condition: the condition is evaluated after the specified event was detected. A condition can verify that a specific Operating System is installed, the VM configuration meets certain criteria and many more
-
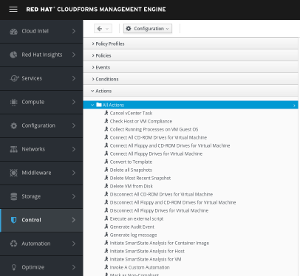
Action: after detecting the event and validating the condition, an action can be triggered. Actions can be specified differently if the condition was TRUE or FALSE. A Control Policy can can send an email alert, trigger a SNMP trap or any customized action. A number of actions are already shipped out of the box and can be found by clicking on Control, Explorer and then Actions in the accordion on the left
The screenshot only shows a subset of all available actions.
Compliance Policies
Compliance policies are similar to Control Policies, but do not listen to events. To validate a Compliance Policy, the user can click on Policy and Check Compliance of Last Known Configuration, or a Control Policy can trigger an Compliance Policy Check as an Action.
Compliance Policies can also mark the evaluated object as either Compliant or Non-Compliant. This information can also be used in Reports and Dashboards for a better overview or to be exported for further analysis. More information about Control and Compliance Policies can be found in the Policies and Profiles Guide.
Create a Compliance Policy for SELinux
To check if SELinux is in enforcing mode, a compliance policy like this can be used:
-
Condition: analyse the content of /etc/sysconfig/selinux and verify “SELinux=enforcing” is found in the file
-
Action: mark the VM as compliant or non-compliant
An example of such a policy can be found on Github
Enable the Policy
To enable the Compliance Policy, it has to be part of a Policy Profile. The example found on Github is pre-configured accordingly.
As one last step the Policy has to be enabled. This can be done on individual VMs or instances or any where in the hierarchy, up to the provider level. Policies are inherited to their child objects, for example if the Policy is enabled on a specific provider, it automatically applies to all objects found on this provider.
-
Navigate to the provider, e.g. Compute, Infrastructure, Providers
-
Select the provider and click on Policy, Manage Policies
- Check the box next to the Policy
-
Click Save
-
The icon shows a yellow shield to illustrate the a Policy is enabled
Verify
To verify the configuration, navigate to a VM or instances on the selected provider. Click on Configuration, Perform SmartState Analysis. Depending on the performance of the environment, this usually takes up to two minutes. In some environments it can also take much longer (in particular on OpenStack providers).
Configuration of Smart State is out of scope for this document. There is a knowledge base article Virtual Machine SmartState Analysis Checklist with some useful links.
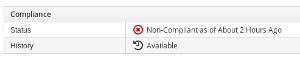
System is not compliant:
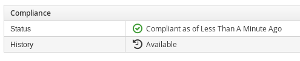
System is compliant: